The events of recent weeks have proven that it’s not a safe world for masculine men out there. Now more than ever men should be looking into increasing their personal security. As an IT guy I have been thinking for a solution to the problems men face. Below are measures I can recommend one take to increase his security.
Disclaimer: this guide caters to Windows users, but others can still find value.
1. Install a VPN

VPN stands for Virtual Private Network. To understand what a VPN does, first you must understand what an IP is. IP is something like a computer passport number. Each electronic device has it’s own IP address. Websites register your IP when you use them—this makes it easy to find your location, your device, and therefore your identity. A VPN makes it so when you connect to a website you first go through the VPN server. So when you connect to a website instead of seeing your computer IP it shows the IP the VPN provides you. Roosh recently wrote on VPNs.
Example (manually changing IP):
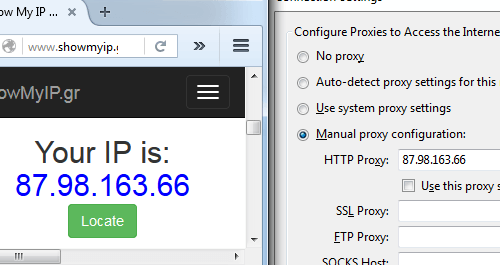
The problem here relies on the credibility of the VPN provider. Many VPN providers register your activity and can then hand it to a government organization if they so demand. Even VPNs that promised not to do this, broke their promise. There is an agreement between the Anglo-speaking countries that affects VPN users. The government can ask the provider for your data, and there is nothing your provider can do to not give it to them.
These countries are referred to as 5 eyes. Currently, similar agreements are being done with other countries, referred to as the 14 eyes: United Kingdom, United States, Australia, Canada, New Zealand, Denmark, France, the Netherlands, Norway, Germany, Belgium, Italy, Spain, Sweden
Definitely get a paid VPN. Free VPNs are not an answer, they most likely register some info on you and are slow. After some research on VPN providers I have found some VPN proviers that are outside the 14 eyes, use encryption, accept Bitcoin, support OpenVPN and have a no logging policy and an overall good reputation.
Here are my findings: blackVPN (Hong Kong, 25 servers, 100 dollars a year), Cryptostorm (Iceland, 13 servers, 52 dollars a year), HIDEme (Malaysia, 85 servers, 65 dollars a year), NordVPN (Panama, 52 servers, 48 dollars a year), Perfect Privacy (Panama, 40 servers, 150 dollars a year), Privatoria (Czech Republic, 12 servers, 23 dollars a year).
One VPN provider attracted my attention particularily, that being BolehVPN, since it is one of the only two providers that offers Tor to VPN alongside VPN to Tor (the other one being AirVPN, which is based in Italy, therefore part of 14 eyes), so if you want that particular set-up, check it out.
Make sure to check the VPN provider’s canary. It is a document that confirms that the VPN provider was not touched by the government. It should be updated every month, if it isn’t unsubscribe. Example.
How to increase VPN security
1) Pay with untraceable money
Sign up for an anonymous e-mail account using Tor and use a Bitcoin Mixer to send Bitcoins to a newly generated address in your local wallet. Alternatively, use the Bitcoin-OTC to purchase Bitcoins ‘over the counter’ from a person, rather than an exchange. Then, use a patched Bitcoin client, such as coderrr’s anonymity patch to avoid linking the newly generated address to any of your pre-existing Bitcoin addresses. —Andrew, Private Internet Access.
2) Make sure you don’t disconnect from VPN and prevent DNS leaks
Use the pro version of VPNCheck to automatically disconnect from internet when losing connection to VPN and to prevent DNS leaks. Or search for the manual way of doing it
3) Use multiple VPNs
Another measure to consider is using two or more VPNs. Basically activate one VPN first, then another one, done.
4) Resolve the PPTP IPv6 VPN flaw
Not likely to affect everyone. PPTP is the weakest VPN protocol and if you use one of the VPNs I mentioned before you will likely use a better protocol, but for those who do, there is a possible flaw that you can correct like this—for Windows Vista and above: Open cmd prompt and type: netsh interface teredo set state disabled.
5) Secure your router
Here’s a guide.
2. Install an antivirus

There are three tiers of antiviruses: antivirus sofwtare, internet suite and premium security suites. Read about them here. At minimum use Microsoft Security Essentials (free software from Microsoft), though paid antiviruses (such as Bitdefender, Kaspersky, etc.) are better.
3. Use Tor and TailsOS for safe web browsing

Many popular browsers are not highest ranked in regards to keeping your anonymity. For example, while Chrome is theoretically secure from spyware and adware, their stance on privacy can be summarized as follows:
He went on, speaking about the future of search. With your permission you give us more information about you, about your friends, and we can improve the quality of our searches. We don’t need you to type at all. We know where you are. We know where you’ve been. We can more or less know what you’re thinking about.
There are factors one must be careful of: cookies, encryption (https), tracking ads, javascript exploits, canvas fingerprinting and others. A writeup on these would take a long time so research them on your own if you wish. I will just mention browsers that avoids these issues.
Use safe search engine
Instead of using the google search engine use disconnect.me installed into Tor (or install as extension into Firefox)
Tor Browser
Tor Browser is an internet browser designed for online anonymity. It is a modified version of Firefox with add-ons pre-installed. Tor works somewhat similar to the VPN concept. Before connecting to a website you go through “nodes”. Which are private stations, each with its own IP. So instead of showing your IP, it will show the IP of the last node you traveled through.
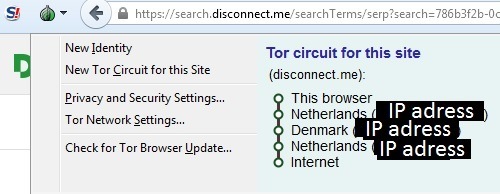
The downside of Tor is that it is slow, due to the fact that it works thanks to enthusiastic individuals. Tor is not for casual usage, but specifically for privacy needs, particularly posting online or searching the deep web.
Tor has some weaknesses you must be aware of:
First
Oftentimes when you are using a network, the network provider can’t see what you are browsing, but they can see that you are using Tor. You can use things like a bridge obfuscator, obfsproxy, or setting VPN to Tor. This is a complex issue, here is a guide on hiding tor usage from ISP (internet service provider).
Second
The trustworthiness of exit relays. When the government found out about the popularity of Tor they created their own exit nodes, that acted as honey traps. To fight this, use a TailsOS (or booted off a flash stick, DVD or SD card in a public wifi spot, like a coffee shop). That way even if the final node was a trap, it would only lead to your TailsOS profile, not your general one. Check so the public wifi spot you are using has no cameras around, so they will not be able to check camera footage of who used a laptop in that particular time frame. Don’t forget to log off when finished. Alternatively, use Tor to VPN.
Third
Often many programs, like torrents, will ignore Tor, even if you manually force them and just connect straight away, thus giving you away. The answer is to not use torrents with Tor. I REPEAT, NO FILE SHARING ON TOR.
There are of course other various vulnerabilities out there. And as a reminder, Silk Road, a large black market was cracked in the past.
Combining Tor with a VPN
Tor is good on its own but even better when combined with a VPN. There are 2 methods : Tor to VPN, VPN to Tor. Both have their weaknesses. First one allows ISPs to see you use Tor, the second does not protect from malicious end relays . VPN to Tor masks your Tor usage, Tor to VPN protects from malicious exit nodes.
I have thought of using VPN to Tor to VPN, which should theoretically accomplish both. For VPN to Tor use a secure VPN provider and add non-Tor traffic to mask usage. For Tor to VPN, pay with anonymized bitcoins and never connect to your VPN without connecting to Tor first.
VPN to Tor: The Harvard bomb hoaxer was de-anonymized because he was the only one in college using Tor. If he went through a VPN first, he would have been harder to track (assuming his VPN provider did not keep logs).
Tor to VPN: Protects from malicious exit nodes, on the other hand. TailsOS with public wifi accomplishes the same. Of course, either is better than nothing. Which you choose depends on your needs. The only two providers that offer Tor to VPN are AirVPN (based in Italy, so part of 14 eyes, but not the 5 eyes) and BolihVPN.
If you don’t want to use Tor
While using Tor is advisable, for casual usage you can set Firefox to be very secure with the help of add-ons and custom settings. Here is a guide.
Websites that ban VPN and Tor
Certain websites ban Tor (e.g. Imgur). Use an alternative then (e.g. Anonmgur). Otherwise use VPN to Tor. There are VPN providers that cycle IPs, so that helps with VPN IP range bans.
TailsOS
Windows is not very safe. There have been rumors of NSA backdoors on Windows devices. Supposedly NSA can store almost everything you do online (including Facebook, popular mail providers, and possibly things offline).
There are some good alternatives out there, TailsOs being one of them. TailOS is an operating system specifically designed for security and is Linux based. It can be ran off a USB stick. For those extra paranoid, use Tor in a public space on a laptop with TailsOS loaded of a flash drive.
Of course TailsOS is not very suitable for day to day needs, so use it for shitlord purposes. For your day to day purposes you might have to use Windows, but for the love of god, DO NOT use Windows 10, it is absolutely awful for security.
I prefer Windows 7. If you are more advanced, you can use alternative platforms like Debian or some distro of Linux or whatever. Just beware, many programs for Windows do not have alternatives on Linux based systems. If you are a casual, moving to another platform can be difficult. And if you really are a nerd, then you can look into some exotic setup like Qubes + Whonix or whatever other myriad of OS and Virtual Machines there are around.
4. Other darknet browsers

I2P network: While Tor is designed to anonymously browse the normal web and onion sites, I2P is a web of it’s own. Preferably to be browsed through Tor. It allows (slow) torrenting and great for messaging, IRC, file sharing, secret websites (.i2p)
Freenet – Freenet is a peer-to-peer platform for censorship-resistant communication.
5. Look into bitcoin and online currency

Bitcoin is virtual currency that has taken the world by storm in recent years. There are other online currencies competing against it, but Bitcoin is the most established online currency. It is the default virtual currency. Bitcoin is not for daily usage, rather online purposes. There are VPN services that accept payment with bitcoin. There are even services that will store physical gold in exchange for bitcoin.
Truly a financial revolution. Unfortunately, it’s also a big headache for tax services. Bitcoin is also infamous for being used to purchase illegal stuff on the internet black market. But you wouldn’t use it for that, would you?
To start using bitcoins just register a bitcoin wallet and you are good to go.
How to increase bitcoin anonymity
Bitcoins are not anonymous by default. They must be washed and anonymized. Buying through Tor + Coin mixing + anonymity patched bitcoin client. Over the counter (OTC) bitcoins are an option as well.
6. Use proper password protection

Never use the same password twice. Try to make it long and contain both characters and numerals, etc. Hint : use L33t, [email protected]|)333. If you can, add non English characters even better, PåSsWøRд0, but you can’t always do it.
If you are unsure, use a safe password generator, such as Master Password To manage passwords use a password manager, such as KeePassX.
7. Use proper mail protection

Use throwaway email to register in most places. Never use your public e-mail to register anywhere controversial like Neomasculintiy affiliated websites.
Safe Mail Providers
For general mail needs, use a mail provider that is focused on security. I found two outside 14 eyes, in Switzerland: ProtonMail (free), NeoMailBox (50$/year, custom domain option ex : [email protected]funny.com, [email protected]customName.com)
Remember to still use personal safety measures, like additional encryption. Never trust 2nd parties with your protection completely.
Become an email provider yourself
Another interesting move is to become a provider yourself, in essence create your personal Gmail by turning your PC into a mail server. To do this, use Mail-in-a-box. They have good guide on their site https://mailinabox.email/.
Use a safe mail client
A mail client is a program that allows you to manage mail from the cloud by saving it locally, by connecting to the email host, such as Gmail. The default mail client in Windows is Microsoft Outlook (which sucks). I will focus on my preffered mail client setup.
1) Download Thunderbird
2) Install the Enigmail add-on, to allow encryption
3) Install the TorBirdy add-on, to make Thunderbird run through Tor
Beware the law
Beware of a law that allows government officials to read any mail hosted online older than 6 months without a warrant. Use an external email client like Thunderbird or Enigmail, download your emails and store them locally. Never leave them on the server.
Email alternatives
Look into email alternatives such as : Bitmessage, I2P-Bote, Retroshare
8. Use encryption for messaging

Encryption is the process of making a message unreadable to third parties. Some programs do it for you, manually you can use a program like GPG4win or similar which uses PGP encryption.
The way it works is this :
1) You create your public key.
2) You digitally sign the information with your private key, so when the other side verifies it with their own public key, they can confirm that it is indeed YOUR public key. (WebOfTrust)
3) When someone wants to write to you he encrypts it using the public key you provided, or the other way around.
4) You then use your PRIVATE key to decrypt the message he sent you.
Here is a tutorial:
Mobile encryption
There are encryption possibilities for your phone as well. First, set encryption on your Android device. Second, use an app called Signal
9. Scrub EXIF data of photos you post online
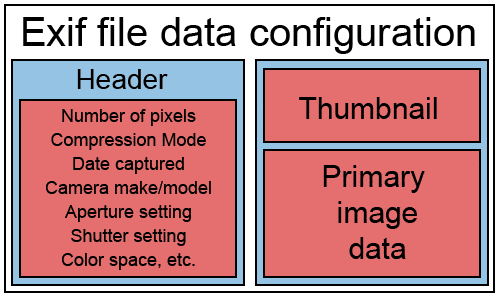
When you take a photo with a particular device, often it registers what device you used to take the photo, when and where it was taken. To avoid this problem, before posting online use an EXIF scrubber. It is a piece of software that deletes all information that might incriminate you.
Some examples are BatchPurifier Lite and Exif Pilot. Also, careful with what photos you post of course, nothing that could indirectly lead to you.
10. Torrent and stream safely
Torrenting can be useful for file transferring. If you plan to torrent anything or share something with friends, look into safer peer to peer torrenting. P2P is good for small files. Generic torrent services are good for larger files.
One advice I have is avoid torrent programs known for their untrustworthiness, such as BitVomit (BitComet) and uTorrent (closed source + adBloat). qBit, Deluge, Tribler (this one’s interesting) are good options (open source and lightweight).
Beware of laws in certain countries that forbid downloading stuff online. Germany is particularly infamous for this. There are ways to combat this issues through VPNs. But DO NOT USE TOR, I REPEAT, DO NOT USE TOR FOR FILE SHARING. For even more secure anonymous file sharing look into I2P (beware avg speed: 30 kbs per sec)
As for streaming, Popcorn Time and other analogous services (such as PornTime) are used to stream new movies (and porn) respectively. They are based on BitTorrent technology. They are relatively safe services, as long as you use a VPN.
11. Encrypt the files on your PC
Use VeraCript, a piece of software designed to encrypt disk partitions or whole USB drives. It is the successor of TrueCrypt (which stopped development after feds asked them to include vulnerabilities).
Hide files in images
Also, another interesting technique is to hide text, videos and other stuff in pictures, it’s called Steganography.
12. Look into this promising new technology for your online needs
The 3 pieces of software I am about to recommend are TOX , RetroShare and diaspora.
TOX is a Skype clone with focus on privacy.
Retroshare is a private network service. You can use it for private mailing and other purposes. Here is a demonstration video:
diaspora is a social network designed for privacy and decentralization https://diasporafoundation.org/
Another interesting possibility for ROK people is to use a .onion or .i2p domain or freenet for a sort of “secret” webpage, unavailable to casuals out there.
To summarize
I think this advice will benefit the ROK community for protecting their anonymity and using secret backup channels for future purposes. Here is a quick cheat sheet:
Casuals: VPN paid with shuffled bitcoin + VPNcheck Pro, Signal on Android, Firefox with add-ons for casual use, Tor for shitlordery, Encrypted mail and hard disk, password manager, ProtonMail for daily use, throwaway mail—everything else, Thunderbird with add-ons, EXIF scrubber. Download email on PC then delete off server.
Advanced: Same as above + Tor combined with VPN, I2P and Freenet, (TBitmessage I2P-Bote Retroshare) instead of mail, becoming mail provider, diaspora*
Super advanced: Same as above + Multiple VPNs, Using Tor off of TailsOS in a public space where cameras cannot film you. Alternative OS and Virtual machines. Secure you router.
Here’s a good collection of security resources.
Always remember, there is no way to remain completely anonymous, just ways to make it harder to be detected.
Read More: 5 Ways To Improve Your Online Game
Sound article with pretty sensible suggestions. While several of the software recommendations are well known pieces of Open Source software it would also be worth making the point that *generally* preferring Open Source software is a sound security and privacy tactic.With proprietary software you don’t know what arrangements the company behind it might have with security agencies, and gurus *can’t check* the source code for implementations of those arrangements, with Open Source you *can* be sure… Open Source operating systems like Linux and the BSDs (especially OpenBSD) are better if you want to take this stuff *really* seriously also.
Anyway, great to see this trend and security/privacy debate happening more and more here on RoK.
Much of the SJW debacle would have been avoided with this stuff in place 😉
Good point. Open Source is the future.
I am looking into the day open source software and OS become mainstream so we don’t have big names like Microsoft or Apple to rig their machines and software on government demand.
that *generally* preferring Open Source software is a sound security and privacy
You’re right in one respect in that some computer geek can see what’s going on. But if Microsoft was found out to be spying or something it would have a big impact on the shares of the co. unless most people are just morons and don’t care.Iphone is more concerned about profits which is why they won’t turn info over the the court.
Good suggestions, but bear in mind that there will counter measures taken. That said, one can safely assume that services like gmail is pretty easily accessible.
Are there any additional suggestions for android phones?
There should probably be a separate article for mobiles.
Though using Signal, and burner phones(for the paranoid() are a good idea.
If you’re rather paranoid, use one of the prepaid providers. They don’t require any name or identifying info, use the towers of the major providers, and are cheaper to boot. Fucks like AT&T and Verizon have been found to have willingly participated with sharing all your personal info to the feds, so the icing on the cake is you get to tell them to shove off (though they are still indirectly profiting from your tower usage).
I use one of these MVNOs for cost and moral reasons, but if you used one and paid with a prepaid credit card, they wouldn’t even know your identity. (I assume they have my name as I pay with my regular credit card, don’t know if they store this info or not).
The best part is, there’s not of that stupid fake “we’re concerned for your privacy” security theater bullshit the regular phone companies have (in college I could never call my provider and ask them how many minutes I used because I wasn’t the account holder–I said do you really think a theif would be calling in wondering if he went over his minutes?!?). Your phone number is your account number and there is no other security, because none is needed. All someone could do is pay on your account if they have your number!
I also heard about some promising stuff in the mobile area and am doing my own reasearch on this topic right now.
ROK writer Thomas More knew we would need to address this issue three years ago:
Yeah, it was pretty predictable given the…. er… ‘distance’ between what everyone’s been told to think and the evolving RoK doctrine… but it’s never too late to learn and apply this stuff and the meetings cancellation and media sh*tstorm will turn out to be a pretty powerful motivator.
Fortunately Open Source has put a pretty powerful set of tools in the public domain for anyone wanting to take security and privacy seriously.
13. Wear an anonymous mask while browsing the internet. It increases your security by 500 %
http://static2.techinsider.io/image/5649d34f112314a8008b550c-1820-1365/6870002408_fb3bb8a069_k.jpg
On a serious note: Roosh mentioned he is planning to create his own microplatform based on GNU social node. He already started with his microblog
That is definitely a good idea.
The internet needs to become decentralized again. Especially since 2016 will be the year of shutdowns. It was great to use big platforms like Twitter to spread our idea, but now time has come to go deep cover.
I want a condom with an anon mask at the tip. This way when I am having anonymous sex I am REALLY having anonymous sex
http://i0.kym-cdn.com/photos/images/small/000/001/122/xzibit-happy.jpg
Bonus +100% security for each chin visible with the mask on.
I would keep your cam turned off and covered too because it can be turned on remotely.
Yes, Big brother may be watching you jerking off lol
This is true. There are programs to spy on you using your PC or phone camera.
It reminds of the Microsoft XboxOne Kinect debacle.
NSA could be checking on me jerking off. I remember how they joked on 4chan that everyone should masturbate in front of the Kinect Cam so that the NSA would be bombarded with dick pics.
Thank you. Thank you. Oh, and, thank you again. This was an amazing article which gave me a lot of info I’ve been looking for in a way that I can understand. I really appreciate this.
Great Article. Pure VPN is best in my opinion for anonymity and security online. I love the software and the ability to select level of encryption.
If you wouldn’t sign your name to it then don’t say it.
Anonymity is for cowards.
That is very foolish. It did make sense one time in this world. But there are a lot of people who could lose their jobs or worse if their beliefs, beliefs that are not malicious but just against the public momentum, should be come public.
Remember that even the idea of celebrating masculinity is a crucifying offense in this day and age. Should we just agree to go along? These ideas need to be made public in a way that will harm the fewest people.
Anonymity is fine by me. In fact, in some ways, it is preferable. Let ideas speak for themselves.
This.
I would like to have agreed with the ‘is for cowards’ sentiment, but for the asymmetric power equation SJW have worked so hard to embed and currently maintain.
This will change…
Correct.
There is a certain beauty about how the US broke off from England. They didn’t hide, they didn’t subvert. They sent a hand written letter, in fucking calligraphy, to the king of England, that began When in the course of human events it becomes necessary for one people to dissolve the political bands which have connected them with another and to assume among the powers of the earth, the separate and equal station to which the laws of nature and of nature’s god entitle them……
How fucking bad ass right. They signed this and sent it to the king.
But time are much different.
Just for saying something against the feminist grain some beta fuck gamer who knows more about computers than I could ever imagine can find out my name, my home address, my fucking credit card number and literally ruin my life.
So I have 2 choices. Shut the fuck up and let them win or continue to speak from the protection of anonymity.
Funny but my mind was on the signing at exactly the same time (and I’m a Brit btw!). It is a perfect example of exactly this nexus. The signers were of course well aware that they could actually have been signing their ‘death warrants’, and I would argue that they, as it turned out, chose pretty much exactly the right time to move from ‘anonymous’ to ‘signed up’…
It really was a beautiful way to announce their intentions. In fucking calligraphy. I’ve always liked that.
Yes, they knew they were signing their death warrant. However, they were intentionally entering a battle.
They didn’t just show up and write that. Years of sitting in the basements and backrooms of public houses, the barns of people they trusted, sympathetic churches, masonic lodges, etc.
The ideas needed to be formed and coalesced under the security of anonymity or they would have been picked off one at a time before they could have had united their purposes and resolve.
Precisely. The. Point.
The Declaration was not the beginning of the fight. July 4 may be the birth of the country, but April 19 was the day it was conceived, via violent doggy style.
Indeed…but the larger point I was getting at was the years before hand where they were in hiding before they were able to announce intention.
That’s because you’re an individual, and in that provocative state you have no choice but to be a coward.
Where’s your gang or syndicate to back you up? Where’s your political power to counter the SJW faggots?
You have none, because unlike your enemies you never bothered to network or organise. You never had the salt to sacrifice the autonomy necessary to achieve a goal greater than yourself. No, collectivism is a great evil in the American conscience.
Ideas are nothing without a man to speak them, and who on earth wants to follow a man who is scared?
dude, really?
allow me to address:
I have no gang nor syndicate nor do I want one.
I have no political power nor am I looking for any.
My goals are all oriented towards my personal desires and, to be honest, I have achieved pretty much every one that I’ve put my mind to.
The left, the right, the SJW’s they can all fuck themselves. What I worry about is some faggot chin beard sitting in the basement who, with only the keyboard that he uses to use redit and look at videos of shit I experience, can literally ruin me. My job, my credit, my standing in society.
Ideas are nothing without a man to speak them? Really? Did you fall down and hit your head.?
Achieved all your goals yet you don’t have the guts to use your real name.
lol
ok
Hey, I’m not the anonymous faggot here hiding away.
Don’t get confused there; the shame is on you, not on me.
Says the guy with a terribly common name, lol. I count six of you on FB. Care to link us to the correct one so we can note your address, place of employment, relatives, etc?
you seem to know an awful lot about me. Congrats Matt Edge on your openness. I salute you. Seems a strange and arbitrary point to take a stand on, but whatever floats your boat bud.
right though? Whatever, he is a troll. Like all trolls, he only survives to the extent that you feed him.
Yeah, I notice he hasn’t returned after I invited him to continue outing himself. Typically ignorant white knight douche.
I guess. They are getting crazier or dumber or both. I mean, this wasn’t even something that would “trigger” SJW wrath. It was just an informative piece on protecting yourself on the internet.
People are so fucked to death nuts.
I know you’re a scared faggot little bitch. After that there’s little incentive to want to know more about you.
Who cares.
At least I have a name, and yes it is my real name.
Facebook? I don’t have one. Not everyone is bullprepping Zyklonberg like the servile Cuckolds you expect them to be.
What’s your real name faggot?
Ok terrific
Cool story bro. Not going to answer my questions, I guess?
Yeah I don’t have a Facebook. .. dumbass.
What’s your name faggot?
Except I didn’t ask if you had FB, “dumbass.” I asked you to prove that you’re Matt Edge. I can claim that my name is Robert Santiago, but until I prove it, it’s a lot of bullshit.
That aside, why would I tell some anonymous grandstanding fuckwit my name? I only introduce myself to people who can a) advance my career or b) I want to fuck. You’re neither, you’re just a douche who thinks that posting his alleged real name on a forum is worthy of respect, lol.
Talk is cheap. Link us your website. Tell us about the businesses you’ve built, etc. Otherwise I’ll just continue to have a good laugh at your raging impotence!
You want to hold me to a standard you yourself are admitting you don’t even have the balls for?
Talk about impotence, you’re still a cowardly hypocrite too scared like a little bitch to use his real name.
Not even all the “10 ways to become an alpha male” articles on ROK could make your balls drop. Take your excuses elsewhere you imposter with a fake name.
You’re the one who came in here blusterfucking around and shouting your “real” name in everyone’s face. So prove it. Oh that’s right, you keep choosing not to.
Like I said, talk is cheap, “Matt Edge.”
lol
“Anonymity is for cowards.”
Man, you’re a dope.
You’re probably going to prove your stupidity by responding to me by saying something along the lines of: “Cry harder Jim Morrison. Lol not your real name of course.”
Cry harder Jim Morrison. Lol not your real name of course.
Hello FBI
And you are…?
…
Exactly.
BTW: on the topic of computers. Boston Dynamics (the company Google bought that makes terminators) released their new terminators today (at least it was on the news this morning.
I wonder how much of that timing is Google reminding the government that they aren’t run by a bunch of fashion people making money as tech accessories and that should the FBI come knocking to ask for access to Google the way they did to Apple they really ought to keep in mind that they have an army of fucking terminators.
It does seem that there might be privately funded/engineered armies in the near future with some of these tech advances. I imagine in a decade or so we’ll be watching news reports of Google, Apple, and the government duking it out.
Cyberpunk was right all along. Megacorporations will replace the government in the fututre.
https://en.wikipedia.org/wiki/Megacorporation
The sad thing is, at this point, it might be an improvement.
Although with current battery technologies, it will be a rather short war.
Wow, what a great, thorough article. Good job man.
Be careful what sites you visit and what apps you use. Something tells me that when an app like Instagram is bought for a billion dollars, with no forseeable way to make money, that it’s really a honeypot used to track and record your location, spy on you with your camera and microphone, etc. Also, when law enforcement looks into someone, the first thing they do these days is examine their facebook account. They can often find more in 5 minutes of browsing than in 24 hours of old fashioned detective work.
I want to mention to the people here who believe that government using big organizations as honey-pots is overly paranoid that it isn’t.
1) Facebook cooperated with Merkel on banning criticism of migrants
2) Certain websites have not been making money since their inception, yet are still kept alive. Aside form Twitter, we have the example of liberal news websites that have not earned a cent since day 1, yet they are kept as propaganda tools.
“It was a big story that when AOL bought the biggest left-wing site of all, Huffington Post, in 2011 it wasn’t making any money. Now, four years later, it still makes no money, according to a comprehensive investigation by the Wall Street Journal. AOL keeps the site alive as a propaganda outlet.
Wikipedia gives us the following on the financials of Salon:
Salon has been unprofitable through its entire history. Since 2007, the company has been dependent on ongoing cash injections from board Chairman John Warnock and William Hambrecht, father of former Salon CEO Elizabeth Hambrecht. During the nine months ended December 31, 2012, these cash contributions amounted to $3.4 million, compared to revenue in the same period of $2.7 million
As we have reported many a time, Salon is the most hardcore Jew site around, and functions exclusively as a propaganda outlet. It is not a business.
The Daily Beast famously lost $100 million dollars under Tina Brown, and it still makes no money.
On top of this, George Soros pours money into Columbia University, and most of the professors then write for these outlets for free.”
http://www.dailystormer.com/left-wing-media-is-collapsing-in-on-itself-because-no-one-cares-about-their-gibberish/
Also, if George Soros is willing to invest millions into bringing third worlders into Europe and US, rest assured he won’t spare millions of dollars to invest into making honeypot websites (he already finances media that doesn’t bring him a penny).
Also, the heads of these tech companies regularly meet with top level government officials (perhaps Mark Zuckerburg just wants regular tours of the Lincoln Bedroom but I suspect something more nefarious).
If you are 30 or older, you remember a time where if a website asked you for personal information like your date of birth or phone number, you would laugh and realize it was a scam. But, like the frog into the boiling pot, we slowly became to accept this obvious ruse. The one that really kills me is sites that want to send me a phone verification code. Why do you need my telephone number?!?
I regularly give fake information to sites that don’t need to know my real name, age, location, etc (this is almost all of them except perhaps my bank). I would encourage others to do the same. There are free websites that can be used as “temporary phones” where they can receive verification codes for you for those apps which require phone verification. Just because everyone is giving away personal info to strangers, corporations, and honeypots doesn’t make it safe and acceptable.
“There are free websites that can be used as “temporary phones” where
they can receive verification codes for you for those apps which require
phone verification.”
I used that to activate a youtube account once.
Spot on.
It didn’t have to go that way…
Bruce Schneider described how commercial transactions could safely and securely be undertaken without revealing the identity of either party in ‘Applied Cryptography’ a couple of decades ago…
That sounds interesting, I will look it up.
Exactly. If you’re not a bank or some other institution where it’s unavoidable, you ain’t getting my real birthdate, phone #, or even zip code.
Same thing with the whole “just store everything in the cloud” push. Couldn’t be any nefarious motives behind that, could there?
I’m glad you chose to stick around despite the alt-right thread shitstorm.
I’m not even alt-right, I just agree with them on some stuff.
The reason I was disappointed was because it uselessly burned bridges. Roosh confused a few twitter trolls for the majority of the alt-right.
The reason this was a little bit disappointing was because many alt-righters were defending him when this was not a popular thing to do, and so I felt Roosh needlessly put a lot of people in a uncomfortable position and his arguments were very weak.
I am still planning to write some articles in the future. A few review of books and maybe something else, I’ll see.
And meanwhile… Breitbart started from nothing and became a huge site in a few years.
Controlled opposition. All part of the plan. Just try saying something critical of Israel on Breitbart and see how long you last.
But I’ll give credit were credit is due.
For a “mainstream” conservative news site they are quite good.
Also it’s a great recruiting ground. Lots of men there are on the fence there. A well done argument and a link to a good article or video will bring guys to the radical right. Good place to shill for the manosphere or the alt-right.
Yeah, there’s a lot of places that have pieces of the truth, mixed in with propaganda or BS or crazy theories, and sometimes you can point people in the right direction. Breitbart is pretty good in that most of their stuff is straightforward. Their big downside is of course the Israel First thing, which is pretty obvious. The other thing they do, which is a little more subtle, is to push the “Evil Islam” thing in a way that’s kind of Pamela Geller or Frank Gaffney-like. That seems to be an intellectual trap to focus people on religion rather than race, plus a way to wind the Left up about “Islamophobia” in turn. It distracts from the obvious point of “Hey, I don’t hate ’em. I just don’t want ’em here. They’re not us, and they’ve got their own countries.” But any non-mainstream site has people that are at least vaguely aware that the standard narrative has something seriously wrong with it, so you can sometimes push people a little if you’re careful.
They certainly are better than most, though. Even Alex Jones can be OK if you ignore the crazy part (and substitute “jews” any time he mentions “Nazis”). For political stuff, theconservativetreehouse is actually very good. They’re patriotards of course, and very much pro-Israel/ jew, but they come up with a lot of detailed political analysis, are very anti-GOPe, and they had only good article I’ve ever seen looking at Benghazi in the context of the whole project of overthrowing Qaddafi, and how Stinger missiles got diverted from that project to Afghanistan to shoot down US helicopters. I don’t bother to comment there, but sometimes I see hints that people in the comments are hiding their power level.
Even NRO, of all places, if you get lucky, you have an occasional chance. TRS/ DS et al are always beating up on them, of course, but the mods took a break for a couple of days or something, and a lot of realtalk was getting through earlier this week. Some guy asked wtf was going on, and why the comments section was such a mess, so I took a break from trolling and actually gave him a straight answer and pointed him to some other sites. Of course, the downside to trolling hard is that it makes it easy for the regular NRO types to dismiss you as a crazy. I usually try to ask questions and bring things up subtly, but it’s usually not worth it at the Kosher Review, since they’re so quick on the trigger, and most of the actual normies there are old and set in their ways.
Soros has been known for creating and funding puppet groups, including ones tailored to conservatives but that openly flaunt liberal causes
http://www.breitbart.com/big-government/2015/11/20/soros-backed-group-launches-bid-to-keep-syrian-refugees-flowing/
http://www.breitbart.com/big-government/2013/06/02/national-immigration-forum-lead-evangelical-jim-wallis-funded-by-george-soros-other-bastions-of-institutional-left/
P.S. never trust anything on WIKI either.
Yes. ‘Social Media’ has made the, formerly spy agency, job of digging up the dirt trivial. Most people *eagerly share* that sh*t these days!
Funny old world…
It reminds me of the mantra, “if something is for free then you’re not the customer, you’re the product being sold”.
Excellent. Where is that from?
What about the free cookies at publix?
The cookies are people!
Online cookies, however, are quite tasty.
Soylent Green
Don’t run the cookies for me
Well I’m using a 128bit Kratom Firewall Encryption.
Think I’ll be safe.
128 bit is weak these days.
I use 256bit Open Red Thai Kratom encryption.
I should upgrade. I’m still on the 32 bit horny goat weed.
Need more articles like this. The more rhetorically or intellectually based opinion pieces are good, but being a man is about more than just having a conversation about culture. It warrants action, and action requires skill and competency. I know pretty much nothing about online security and such, so I have no way of evaluating the objective worth of this article, but just so long as you have pieces that discuss these sorts of things, and encourage men to develop their own proficiency in areas that impact their personal lives and communities, whether it be fitness, technology, finance, professionalism, or whatever, you’re doing what needs to be done.
All of this. Good write up.
In my opinion, #9 is your most vulnerable. Exif has been around for a long time. It could put your GPS coordinates depending on the software you are using. Scrub that crap out.
Yes, and it is rarely mentioned to boot.
2016 will be the year of shutdowns. It is time for the internet to become decentralized.
We had fun using Twitter to spread our ideas, but now it is time to use our own microplatforms and amp up the security.
Roosh already has a microblog and he promised to make a mini-platform using a GNU Social node, so that is good news.
We cannot stay out in the open anymore, it is time to go deep cover.
I’ve never used bitcoin or any other digital currency. I wish there was a good, stable, anonymous digital currency. The price of bitcoin fluctuates wildly. Plus they are still regularly creating more of it, although that should slow in the coming years (currently has an inflation rate of 9%, should slow to under 2% by about 2020 https://en.bitcoin.it/wiki/Controlled_supply )
Digital currency creators should understand that stability is one of the most important components of a currency! It’s the main reason the US dollar has been accepted for years in so many of the ‘banana republics’
Stability can only happen through government intervention. For bitcoin, it will only happen when it is as widely adopted as it is going to be.
Stability sucks anyway when the long term direction is up. Buy now and wait five years. Or half a year, if the halving does what some people think it will do.
As far as anonymity, bitcoin can be if you do it right. But besides that there is monero (which I don’t own, just tossing it out there).
That’s not the “only” way stability could happen. For one, they could stop issuing more bitcoins. This is already happening (essentially new bitcoins will stop being issued in 2020). So I predict the value of bitcoins will be more stable going forward than it has been in the past.
Another idea would be not allowing essentially “day trading” of the currency. For example, you look at how mutual funds are traded versus stocks. Mutual funds have a set price for the entire day, while stocks fluctuate in nanoseconds. Of course the *value* of the underlying company didn’t change in that microsecond, but the wall street casino allows it to trade that way. Same with bitcoin.
Another way would be to make it appeal more to shoppers instead of geeks and bitcoin “miners”. Imagine if Amazon created its own digital currency, and it was designed to be appealing to people who shop there, as opposed to people with 8 video cards in their system mining digital hashes.
There are certainly ways one could design a stable currency without having a government involved. However, having a government issue money does ensure some degree of permanence. Ie bitcoin may disappear in a year but I seriously doubt the Canadian Loony will.
Finally, while everyone wants something they own to be more valuable tomorrow, money must meet 5 criteria:
The characteristics of money are durability, portability, divisibility, uniformity, limited supply, and acceptability. Appreciation is not a quality of money.
Surprisingly, even the federal reserve still believes in this definition of money!!!
https://www.stlouisfed.org/education/economic-lowdown-podcast-series/episode-9-functions-of-money
They can not stop issuing coins. The 21 million limit is an integral part of what makes bitcoin bitcoin. Miners would never play along, and even if it happened confidence would be completely lost. It also would do nothing so far as stability, the price is a direct result of supply and demand.
You can’t stop trading without shutting down the internet. Nor would most of us want to. The ability to handle your money in exactly the way you see fit is another huge selling point.
The fact that bitcoin can not be created or destroyed on a whim, and that there is no central authority, is why many of us will never trade it in for amazon tokens. On a side note you can no longer mine at a profit with gpus, those days are long gone. And people can and do use it to buy stuff.
There are in fact stable altcoins. People don’t want them. The experiment has been tried and failed.
Explain how bitcoin could “disappear”.
Taking anything the feds say as support of your case is generally a poor idea in todays economic reality.
According to the bitcoin link I posted, 75% of all bitcoins are currently in circulation. The remaining 25% will be mined at an ever decreasing rate. No, mathematically they will never stop issuing coins, but essentially in practice they will, because when 99.999999% of all bitcoins are in circulation, the effect of increasing the supply ever so slightly has no measurable effect.
Look into how mutual funds are traded. The internet is not shut down. They just don’t allow the prices of mutual funds to fluctuate daily. You place an order, your order clears at the end of the day at a fixed price. The same could happen with digital currency. Just one of many ways to avoid price instability.
All the alternative coins today use the same model they ripped off from bitcoin (ie based on a mining system, with a blockchain, etc.) It’s a very brilliant system, but it’s far from the only way to operate a digital currency. I’m fully convinced the idea will evolve and improve in the future.
Bitcoin could disappear in many different ways. The most likely of which would be creation of a new and better digital currency. I haven’t followed closely, but I’m sure at least one of the alt-coins has failed and disappeared by now. There is nothing to guarantee bitcoins will be around in 100 or 10 or even 1 year (thought over the short run it’s obviously quite likely they will continue).
That’s a silly argument. The concept of the 5 principles of money goes back centuries. Just because the fed agrees with a universal truth doesn’t make it a lie. By that rationale it’s a “poor idea” to call today Wednesday because the gummint thinks it’s Wednesday too.
Digital currencies have yet to go mainstream. Basically because they lack the stability and ease of use of standard currencies. If I want to use my debit card to buy groceries at the store, I don’t have to worry about how the value of my funds have fluctuated since I entered the store. The value of my money is stable. I know a lot of bitcoin enthusiasts get off on the price fluctuations, but understand that this is actually a negative function for currency to have, and most people are scared by this.
Coins will stop being mined around 2140.
Mutual funds have a central authority. Bitcoin does not. Simply saying “don’t allow…” is not enough. Propose how restrictions to disallow it would come into place.
Changing from bitcoin to something better is not the same as bitcoin disappearing – it is moving on to something better. For something to “disappear” implies that it was a bad idea and has been abandoned. The idea itself is a revolution on many fronts. It will not simply go away now that the tech is out there.
The dollar is not money. It is just currency. Money keeps its value. The dollar has lost, I believe it was, 97% of its value since going off the gold standard.
Bitcoin is immune to inflation. Just ask any argentinian who uses it.
The very fact that bitcoin is not yet mainstream makes it a good idea to invest in. When your taxi driver or your hair dresser starts talking about investing in it, then is the time to sell (some, never all).
It’s speculation all the way to the top. There is no way around this. If you disagree then explain why and how, don’t simply say “nuh-uh”.
The Mount Gox issue caused a huge drop in the status of bitcoin, and could have been its end. I don’t think bitcoin is going to disappear, but there is a significant possibility that it could. I’m also more of a wait-for-gen-2 kind of guy. Ebay improved on yahoo auctions. The Apple Newton went nowhere. So basically I’m waiting on someone to come along and take the brilliant idea of bitcoin, address its shortcomings, improve on it, and produce a new killer currency. Off the top of my head I would say make it more private, more stable, and more easy to use, and you would have a game changer.
The US Dollar is a really bad monetary unit, but it is among the very best options that we have today. As far as the fluctuating value issue, you really can’t envision a way to create a currency that doesn’t have a constantly variable value? That’s a little outside the scope of a discussion on a masculinity website, but i’ll just say I have a few ideas, and I see no reason it would be impossible. There are a lot of really really bright people out there in the tech world, and I don’t see this as a problem they couldn’t address.
Gox was like a bank being robbed. It has nothing to do with bitcoin itself, just some of the market. These things are generally seen as positives on the long term by the community because it proves that we can get past things like that and makes us more careful about security in the future.
Unlike social networks, people have real money tied up in bitcoin. Actual value. It’s not just some fad like your examples, it’s a new kind of money with unique properties. Due to the network effect it will require some seriously improved features for any other coin to supplant it. I have not even heard proposals for what those might be yet. The usual analogy is IPv6. It’s better than IPv4, yet failed to gain popularity simply on technical grounds.
You have yet to explain how the stability you keep mentioning could happen.
Fantastic article, but none of this should be required in an ideal world, and, quite frankly, this is complicated, and most people will lose vigilance and fuck up somewhere. Realizing that we don’t live in an ideal world, let me also make a suggestion to get us moving back in that direction: if you are a man in a position of power, refuse to cooperate with an SJW witch hunt. If you receive complaints that a man beneath you has broken some arbitrary hurt feelings rule, and the mob is demanding his head, tell them “no.” If they threaten a boycott, tell them to bring it on. The hurt feelz brigade was up in arms over Truman Cathy’s views on fags, but last I checked, Chick-Fil-A is still serving plenty of tasty sandwiches to dudes like me who don’t give a fuck. Most of this outrage is toothless posturing by cowards. Don’t bend to it. Support men who are under attack from it by protecting them if you are in a position to do so, or buying their products and services if you are not. Stand shoulder to shoulder and back to back, face these fucks head on and help your fellow man become anti-fragile. In short, make this article obsolete by returning to a same world where we can have honest discussions about differing opinions without having to worry about anonymity.
I especially like Protein World’s response to all the outrage to their ad beachbody ready with the girl in a bikini. They basically told the SJWs to go pound sand.
Yeah, that was also hilarious. And good on them, I don’t know many people who aspire to look like fat land-whales.
I don’t read it but I heard that Sports Illustrated used a fatty on their cover of the swimsuit edition. Is that true? Pirelli did something like this too. You should all buy these because they’ll be collector’s items after people come to their senses and reject this crap. They’ll become like rare baseball cards esp. Pirelli because these calendars are in limited editions andonly given to their top customers who sell their tires etc
I distinctly remember when the whole Chick-Fil-A debacle happened. I went to my local one to show my support (and eat a tasty chicken sandwich) and the place was so insanely packed, it took me 15 minutes just to get into the parking lot. The drive through was wrapped around the block.
Of course! Delicious chicken tastes the same regardless of whether the person making it thinks fags should be married or not. Smart people understand this.
“Of course! Delicious chicken tastes the same regardless of whether the person making it thinks fags should be married or not. Smart people understand this.”
Anti-sodomite chicken tastes better than pro-sodomite chicken. Any person who thinks sodomites should be allowed to be legally/socially recognized as married is mentally ill and is far more likely to have communicable diseases and hygiene issues. Pro-sodomite “chicken” from (insert corporate name that is publicly pro-sodomite) probably isn’t even real chicken to begin with and things only go downhill from there.
There’s some truth to that.These radical pro homo marriage places may go out of their way to hire homos.
Anti-semite chicken is even healthier because it’s baked in an oven.
Chick-Fil-A: Delicious chicken sandwiches AND standing against gay homo marriage.
What’s not to like?
Every Chick-Fil-A I’ve been to is always that busy during the lunch and dinner periods. One I visited even had markers in the parking lot noting 15/30 minute estimated wait times, and cars were always wrapped around even further. It’s great.
I usually swing by at like 4pm to try to get my spicy chicken fix between “rushes” and there is still a wait.
Sometimes bad publicity can do wonders for the bottom line.
Wanna know how I found out about ROK? From a Change.org petition calling for Roosh to be banned from entering Canada for a meetup. No. I didn’t sign it.
If you live in any big city in america now, the SJWs are just background noise on the street. You can’t live your life worrying about their next protest of the moment, which will disappear as quickly as it emerged.
Their protest usually consists of a dozen fairies, dykes and some crazy cat women femtards. All they do is try to annoy people or even cause damage and after the cops arrest them they’ll scream police brutality.
They opened a chick-fil-a in nyc I believe and it received a lot of press; good press. People wen my bananas for it. And considering how sjw nyc is, the food and saying “no” to the mob speaks for itself.
Chick-Fil-A has long lines at libtard central (NYC) waiting to buy the stuff. The libtards must be pulling their hair out lol
Very comprehensive article!
The info was already out there on the net for anybody who wanted to find it. This just makes ROK look suspicious. Its better to stay in the open as long as you’re in a free speech country like america.
http://www.facebook.com/Feminism-is-a-lie-357374801138236/
This is good stuff.
Drop social media and you drop most of your problems . Don’t know why you would need alot of secrecy unless you’re going to extremest sites , buying things off silk road ,or something along those lines . I use the internet for porn , this site , work out tips , and gaming . Don’t say anything you wouldn’t say to a person’s face and don’t have creepy fetishes and you don’t have anything to worry about .
You are exactly right, but, for instance, where I live ROK would be considered an extreme site.
I don’t think this site carries nearly as much weight as lurking storefront
No, of course not. But let me give you an example of a very real possibility.
I make a comment about some faggot SJW and his enabling absurd feminist causes.
Next, Roosh flames some cunty feminist site.
That flaming drives a ton of troll traffic to ROK
In the process of talking about how we should all be castrated for hurting their feelings they see some of my comments.
They are triggered.
Some blue pill douche stops playing war craft for 3 minutes in order to come to the rescue, white knight style, in the hopes of getting some attention from the girls.
he “doxes” me (a term I didn’t know until someone here explained it last week to me).
He is good with computers and follows up.
Now he knows my name, address, employer, my credit card numbers…I don’t know…I am a tech moron…
He posts this information at femincunt.whatever
ALl of a sudden my employer is being inundated with calls that a horrible, misogynistic, anti whatever jerk works for them.
I have several deals going on with the city that are now in jeopardy because my company can’t be seen harboring some “rapist” blah blah blah
Now I am out of a job. I go to my security blanket to cushion my finances while I look for another one, but my cards have all been maxed out on anal butt plugs.
My credit score has been tanked.
I now have no job and need an attorney.
Moreover, I am applying for jobs and every time a potential employer googles me they find out that I am an evil rape apologist. Believe it or not, care or not, they don’t need the extra heat when 10 other guys are applying for the same job.
Is this likely? No. Is it possible? Abso-fucking-lutely. And, if for 40 bucks a year I can make it totally impossible with no down side…then shit, why not?
If you’re using a throw away email address from yahoo, and aren’t using an avatar pic, nobody really knows what you’re doing on ROK except homeland security. You want a new IP address, just unplug your modem and/or router for 24 hours and it should re-set. Also any wifi enabled coffee shop gives you a new IP adderess while you are there. This ROK article was over-kill.
Fair enough . If one of those “doxxed” me . I’d just do what the Mexican cartels did haha. Minus the leaving them dead in a ditch part
yeah, but for 40 bucks a year and 10 minutes of configuring why take a chance right?
Off topic, but why the avatar pic change? Increasing your anonymity?
actually, I saw the simpsons episode last night where it is shown that the power plant is technically in the name of a Canary named Canary Montgomery Burns for liability purposes.
Made me laugh so I used it.
Hah, gotcha.
I figure most people aren’t going to care enough for us commenters….we’re pretty low on the chart in regards to ROI.
Didn’t they sabotage the exportation of avocados and make oodles off ’em a few years back?
Homeland security would give ROK a curt nod and chuckle at the feminuts. They have more important things to worry about.
Although the rumors of JADE HELM 15 aren’t pleasant to think about…
Don’t know about that . I was talking about when anonymous threaten to doxx them so they hired their own hackers and threatened them
Some blue pill douche stops playing war craft for 3 minutes in order to come to the rescue
Why aren’t you beating these white knight omega pajama boys up? These were the mama’s boys who the bullies would give wedgies to and steal their lunch money; keep up the tradition :o)
Most of these cellar dwelling lardarses were the losers and now they think they can get revenge anonymously over the Net. Teach them that they can’t.These weenies will stop the first time they get a broken finger.
I still don’t understand how anyone would know your identity unless you’re giving something away.
You turn it off for a few minutes and usually get a new IP. Just check your IP here or in other places.
http://checkip.dyndns.org/
Both of your comments make sense to me. I don’t understand either. But people I trust say that while I was being me these geeks we’re learning this stuff. I don’t get it at all. But if I can throw 50 or 60 bucks a year at making sure it’s a non issue its not even a question
Great article. Probably one of the most useful articles I’ve read in a while.
I surf at work so, the vpn info was eye opening to say the least. This was very helpful and informative.
There is no such thing as internet privacy, or anonymous internet use. Post 9-11 and post second edition of windows 95 actually there are backdoors, and digital DNA used to i.d everything and every connection no matter wtf you use..!! . Post 9-11 all ISP’s and server farms were forced to install software by the NSA which guaranteed the death of privacy. I forget the last holdout at the time but they posted that they were forced at basically gunpoint, and that all communications were compromised on out… Now all chips come with firmware they can track bits of data all over the internet. Your PC/Laptop is a huge information sieve that drains right to Utah’s big data centers…There is a digital carbon copy of everything on your hard drive./storage. If you want total privacy. Do not use the internet.
This is one of the best Internet-use articles I’ve ever read, if not the best. Thanks a lot!
This is great primer for gaining anonymity in the Internet in this day and age. In the early days of the Internet, anonymity was king and share your information to chose few, Now everyone wants to know everything detail of your life to make a quick buck off of you or destroy you. For anyone look for good Linux distro, elementary os is pretty good.
lol, too late
Been posting with name + photo for two years now and nothing’s happened so far cept a few barely coherent phone calls to my office number.
But someone has approached my little brother and given him shit for being related to me so maybe i do need an anonymous profile pic
That’s grounds for retribution in my book. What scum.
I don’t mean to be flippant or derogatory, but, I’d never be able to identity your face in any distinctive manner on a city street from your face pic. You look like a thousand random faces, no better or no worse (I mean this a non-personal way).
well the guy who approached my brother could tell – he does look alot like me, but less ugly
“do you know an internet asshole named Terry?”
“yeah he’s my brother”
kid’s kinda dumb
Small world, hey! I don’t think I’d ever recognize another person’s this way, besides, you could use the face pic of your worst enemy too.
Now I feel like Evil Knieval for reading Return of Kings with people on either side of me while waiting for class to start.
So you did publish the article. Good work.
one of the most informative articles I’ve ever read on privacy, so thanks for that. I would say though that the best non-technical defense is to comment in such a way that you always feel confident that were you held somehow accountable for your speech you would be able to fully justify what you have said. Obviously, with respect to the possibility of consequences for employment etc that doesn’t apply, and it’s appropriate to seek anonymity, but since anonymity will never really exist in the sense we’d like it to, it seems to me better learn the discipline of arguing your case as though it were always something you could defend publically, without shame or apology, which is really to say, we should both look after our privacy / anonymity (using guidelines such as these) while arguing our case cogently. This is easy to do, just imagine a blue-haired harpie in your minds eye who knows who you are, and would just love to get you into trouble, and make sure you use such arguments as would make her powerless in her every screech to indict you in the court of public opinion
BTW tails was what Snowden and Greenwald were using I think, so it should be fit for purpose
Question: If you reside in a country outside one of the 14 eyes, but, the VPN being used is hosted in one of these countries, do they legally have the right to furnish the user information of a non-eye country citizen to a third party government? Could they be sued if this was occurring?
good question. I always assume that if the server is physically located within a 5/14 eyes country then it would be subject to the law of the land, regardless of where the company is registered, hence the need to choose your server carefully
Well, I don’t live in one of those States, so, I’d consider it to be a violation of my natural right of privacy if this information was passed onto third parties without my consent. It doesn’t bother me per se, but, I’m curious about the legality of this mechanism in non 5/14 eyes country. I’d imagine my server is physically within my own country where this information cannot be furnished even to my own Government without my consent.
Facebook and Google are currently being challenged by the Data Commissioner’s Office in my country by an Austria man who’s claiming that under EU law the collecting his private internet surfing, e-mails and tweets by the above organisations, and the furnishing of this date to 3rd parties is not allowed. It’s likely that he’s right and his “right to be forgotten” and “right to anonymity” will be upheld by the EU eventually.
I always assumed you lived in England, or perhaps Wales. Yes, I think this whole war on terror shambles is slowly eroding many of our basic rights including with respect to privacy & free speech. Re. intelligence, where legality comes into it, I think its a bit like science, where, when it comes to the write-up, and the author has to demonstrate that an appropriate procedure has been followed, he writes it up in the correct i.e. formal manner but when it comes down how discovery is actually made, in the case of intelligence, what kind of information is shared, what kind of pressures are applied, I imagine it is closer to what might be called methodological anarchism.
Ultimately though online intelligence, surveillance etc isn’t about throwing the book at people for the most part, but just keeping an eye on things, shaping behaviour, preventing misbehaviour. The eye doesn’t necessarily have to be all-seeing as long as there’s a good possibility people think it is. On the other hand, the technology for total surveillance is pretty much there I imagine.
Good on yer non-Austrian for making that challenge. To think there might actually be some use to EU law occasionally
Should be irrelevant as good VPN services do not keep session logs.
“If you reside in a country outside one of the 14 eyes, but, the VPN
being used is hosted in one of these countries, do they legally have the
right to furnish the user information of a non-eye country citizen to a
third party government?”
They can, but there is a question if they would. If your VPN provider is in the UK for example, the government can take the data about you, the question is will they give it to YOUR government.
I think it depends, if the UK thinks it is in their best interest to do so(like if you are terrorist planning to enter the UK for a crime) they might tell it to your government or if YOUR government demands it from UK officials they might provide it or not, depending if the country asking is an ally or not.
The UK would not likely hand info on you to an enemy government, but might do so if they see YOUR government as an ally or they see you as a threat to the UK.
Bitcoin records everything in the blockchain and as recent successful criminal prosecutions have shown, not anonymous.
1) This is probably the only trustworthy VPN guide –
https://torrentfreak.com/vpn-anonymous-review-160220/
2) Freenet is a desert. 99% of resources are dead
3) Antivirus is, at best, a second line of defence. Your primary should be a good stateful inspection personal firewall. These will alert you of anything new on your system attempting to make an outbound connection and ask you to approve/deny.
4) Look stuff up on schneier.com – usually you’ll find discussions vivisecting products/services
5) Ditch Windows/Mac and learn to use Linux. Ubuntu is a relatively painless alternative, but there will still be a learning curve – as well as some lockdown steps like disabling Amazon integration.
6) Whonix is rather nice – sort of like a persistent version of Tails and, because it’s a virtual machine system, allows you to make snapshots to revert to and undo sessions if you are paranoid.
https://en.wikipedia.org/wiki/Whonix
When using shit like this ALWAYS follow the download signature verification steps. And don’t do stupid shit like using Tor sessions to log into your Facebook account. Duh.
https://grugq.github.io/blog/2013/12/01/yardbirds-effective-usenet-tradecraft/
Good article, gives me an idea for some future articles.
IMO the best way in my opinion is to not use your real name on Facebook. Too many dumbasses write non-PC comments on Facebook, but with their real name, place of work and even their address sometimes. Then rabid SJW mobs attack that person and attempt to destroy their life. These people often have pictures of their children too, thus making them potential targets for SJW extremists like Black Lies Matter.
Personally, I am been trolling Facebook for years and nobody found me out. I find it hilarious when SJWs are raging about my posts, then they are attempting to find information on me but only have my fake name.
Never do personal surfing at work. Even if your workplace has a relatively relaxed policy (“everyone does it”) and minimal site blocking, just don’t do it. One letter from a pissy feminazi can get you fired on the grounds of “using company equipment for personal use and/or inappropriate internet usage”. Just ask Michael Nolan.
Of course, using your real name for any dealings with feminists/SJWs is like going to Bangkok without condoms.
You do realize the minute you sign up for Comcast (or w.e internet provider) they can automatically know/see what you’re doing? It’s pointless lol
If you use VPN or Tor, then the only thing an ISP sees is that you connected to a VPN or Tor, that’s it. They don’t see what happens afterwards.
Well, finally… DEEDS OF A GOOD MAN !
I don’t get it, VPN to Tor means he went through VPN first, right? You said that VPN to Tor masks your Tor usage and Tor to VPN protects from malicious exit nodes but not from ISP seeing you using tor.
He DIDN’T use VPN to Tor, that’s why he got caught.
“VPN to Tor: ” was just the header, the body is about the importance of using VPN to Tor if one doesn’t want to get caught and The Harvard bomb hoaxer was an example of what can happen if you DON’T use VPN to Tor
Thanks, I was reading this section of article wrong way.
You know, using VPN to Tor with colon in same sentence with Harvard bomb hoaxer.
6. Use proper password protection
Yes, never reuse passwords, but the rest of the section is wrong. The best idea is to use a password containing 4-5 words generated from a list(2000+ words). The security of such a password is better than a simple word with leet replacements or foreign characters. Also KeePass, while a good idea in theory is a bad idea in practice because it is targeted by several malware that steal passwords from it. Also, if your machine is compromised you can assume that the attacker has access to the contents of your KeePass as well.
Mixing up letters, symbols and cases has always been better than using letters alone. A 14 character password made out of lowercase letters can be brute-forced quicker than a 14-character password containing a mix of characters and numbers + symbols.
4-5words passes are more powerful becasuse they are longer, but you can make a leet password longer as well: appleTreeTireTimeWeasel is weaker than @pPl3Tre€€Tir3TIm3VVæzel# . It is a choice of convinience, of course appleTreeTireTimeWeasel is more powerful than @pP|3 alone, but when it is somewhere in between, things get muddy, so I would say it’s a matter of preference.
You are correct that someone might compromise your PC and get acces to Keepass, but then one might just store his passes on encrypted removable media, like a flash drive.
I am not aware of Keepass vulnerabilities, could you link some info ? Also, what is your proposed alternative ?
Remembering hundreds of complicated passwords is unrealistic, storing them on paper is not a very smart idea either, what do you propose ?
The solutions are oriented towards newbies, and is better than nothing. Do you use something more advanced ? What’s your method ?
Very good information from the author here, and very well-written article.
This is kid’s stuff that we knew 20 years ago.You can’t trust any of these things and I’m not going to take the time to explain it here.Even if I were to scan for active open ‘anonymous’ proxies I’d never know if it was a honeypot set up to entrap the naive and if it’ seems too easy it probably is;aside from that it slows you down to such an extent on the throughput that it’s not worth using.
Since I was one of the first people to use highspeed the network was set up, probably for security by the ISP, so that my IP is not where I am and just comes out of some transfer node but can still tell you that if the CIA or someone wanted to locate me they could.Since I’m not doing anything other than exercising my 1st amendment right I don’t even give a damn.If I ever was interfered with for some frivolous reason I’d sue and make some more money since they’d have to settle after I filed a lawsuit in Fed Court.
Now, the only way it would be almost impossible to track you would be to use some open server or wifi and of course today you have to be sure that you’re not on cam which are either inside or on the street.And let’s remember that if you’re just expressing an opinion that you’re not doing anything illegal so it’s not like some Homeland Security had a gazillion people looking for you or are going to waste resources looking for you.
Put a more powerful wireless card with an antennae on it to pull in open servers at a greater distance.
Pay for things with an Amex card etc. No dummy, not a regular one but a prepaid gift card type where you can use any name etc that you want(you have to pay in cash for these anyway) Still look out for cams when you buy one. OK I’m into paranoia here lol
Hmm but what if you had complete security as a hypothetical but they could still find you by your computer? You may be transmitting your hard drive ID # and it’s easy to match that with a certain model it was put into and that model was sold to Joe Blow. Buy everything cash and never register the PC for warranty etc And even with cash you still may be on cam buying it. They can use face recognition and match you to your driving license pic haha
Of course none of this is going to happen unless you’re public enemy #1 or well up there and they’re looking for you.
On the topic of Windows 10, the thing is that soon Windows 7 is going to lose all support, plus they already have updates for Win 7 that add some of the same or similar vulnerabilities that Win 10 has.
I recommend if you upgrade to Win 10 (which I have and I can’t go back now) watch Youtube videos on how to maximize your privacy and shore up the areas of vulnerability. You can disable Cortana and I believe most or all of the troublesome programs. A program that is recommended to download is Spybot Anti-Beacon which intercepts and disables the telemetry for data collection.
Just food for thought.
Good thought. Yes, there is a guide on making Win 10 safer.
https://www.privacytools.io/#win10
As for Windows 7 losing support, I’ll just stick to it as long as I can.
Windows 7 is on extended support until 2020. As long as you have the license sticker for windows 7 on you computer, you can reinstall 7 again. If you don’t have an instal disk for 7, you can make one by downloading a windows 7 ISO file (has to be the same version that your license sticker says, ie, Home, Pro or Ultimate) and there are free programs online that make it bootable.
I bought an Office Refugee (second-hand computer that was previously leased to a company) that had a Windows Pro sticker on it and upgraded it to 10 just to see what all the fuss was about. Totally hated it and reinstalled 7 using the above method.
Extended support W7 ends in 2020. Allot can still happen in 4 years, both good and bad.
The best way to not get high is to not smoke weed.
Really, that is the best security — don’t be a “user”.
The only other REAL option is to actually understand all those security terms and be an expert, AT LEAST to the point where you can mansplain the Diffie-Helman key-exchange by memory. If you can’t, then quite frankly, all those steps are useless if you don’t understand them.
The security hole is in the mind, not the technology.
i use VPNs and Tor
mainly for the fact i have controversial political opinions ( on race etc ) and in the UK you can get prosecuted for “inciting racial hatred”.
Two thumbs and two big-toes up! Pretty much everything a privacy wonk needs to do is right here in this article. Thanks for sharing.
That is some precious information. Thanks for taking the time to share your expertise with us, August!
I’ve used TOR for some time now. But there’s a program used to watch you from a distance as you type on your computer. The person sits close by and films you, and then the program is able to interpret pretty closely what you typed. It was in the news a couple of years ago, and when people started talking about it, it suddenly dropped out of the news. Which makes me think it’s being used and they didn’t want the public to panic about it.
One year later, is all this info still good?